Cyber-attacks have become increasingly powerful and are growing at an exponential rate, with India seeing a 37 per cent increase in cyber attacks in the first quarter of 2020, as compared to the fourth quarter of 2019. These attacks are starting to pose a higher and more relevant threat to firms each day; data breaches can pose a real threat to not only the firms but also customers, who are at the risk of getting important banking and personal information leaked at the hands of malicious hackers. Data breaches in top firms, such as Marriott International and Yahoo, have leaked the personal details of around 500 million users, leaving customers vulnerable to threats and the substantial risks posed as a result of the disclosure of their banking and personal details.
Crisis can have a lot of risky effects, from losing customers, profitability, and market share to declining stock prices and job losses. In fact, according to a cybersecurity analysis prepared by Ponemon Institute, the overall cost of cyber-crime in 2016, fluctuated from 270,000 to 73,000,000 million dollars a year. To top it all of, it is estimated that 68% of the funds embezzled by cybercriminals are never retrieved again! Not only are financial costs an adverse effect of a cyberattack crisis but organizational reputation is also greatly affected. With all the unfavourable consequences of cyberattacks looming over everyone, from multi-billion dollar firms to the average Joe customer, the need of the hour arises – cyber risk management. Corporate risk and resiliency planning are important for organizations to be able to overcome disruptions from cyberattacks and thus retain stakeholder confidence. Firms must understand and identify potential adverse events in computerized networks to be able to plan and implement resilient mechanisms to defend, detect, and remediate from such threats.
It is extremely valuable for firms to plan for cyberattacks and have cyber security risk management in their planning stage itself, as when a data breach occurs, post-crisis communication is perhaps the only opportunity that a company has to repair its reputation and save its customers. Being able to identify as well as plan for potential threats of cyber risk can help in the long run. Firms can do this by carrying out a risk identification process wherein they assess their current cybersecurity levels and recognise what further steps can be taken to tighten security levels and create new plans, policies and procedures for the same. This can be carried out through cyber risk scenarios in a stimulating environment to assess the current firewall softwares and security programmes. Flexibility is also a key – in a world with ever – changing contemporary technologies and tools for hackers to hack into the even most advanced security systems (the White House has also been breached!), constantly and consistently having a cyber security team to keep updating the strategies goes a long way. A good estimate is to update cybersecurity strategies every 1-2 years with a skilled cyber security risk management team.
Ranging from simple authentication techniques to even more complex tools, companies today have a diverse range of software and programmes that they can purchase and implement to tighten their security system, based on the budget and the size of the organisation. Firstly, all firms must establish a zero-trust security framework – these enforce strict authentication requirements on all users, therefore ensuring that no unauthorized user can access the system. It’s rather surprising how tight security must be maintained even for the internal employees of the firm. In fact, in its most recent annual report on data breaches in businesses, released in May 2020, Verizon said that 30% of the 3,950 breaches it documented during 2019 involved internal actors! 1 Since internal employees of a firm are aware of the ongoing processes and workings of the company, a backup of all the messages that are exchanged between employees should be maintained. Moreover , a check on how they use the company’s passwords and how they keep them safe from unauthorized personnel should also be monitored. In this case, a company, during its planning stage, can purchase a Password Manager to keep track of all the password generations and management within the firm. Firms can also utilise two-factor authentications and ensure a strong sign off policy for their management during its day to day functioning to avoid the risk of internal hacking threats and attempts.
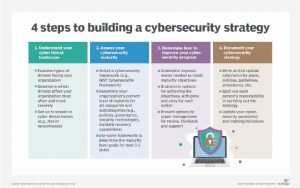
Additionally, firms can hire professionals in their planning stage, such as Cybercrime Consultants or Risk Mitigation Specialists, to regularly carry out risk assessments. The more knowledge they have about the cyber risks involved in their business, the better security measures they will be able to take for their company (no wonder Cyber security and Cyber Risk Management professionals have a 0% unemployment rate!) These professionals also offer knowledge on compliance with voluntary frameworks (such as the Cybersecurity Framework offered by the National Institute of Standards and Technology) which can be used for risk assessment and other related practices. They can help the company’s management and shareholders understand the nature of the business and conduct research about all possible threats that might harm the corporation. Firms must also plan for systematic audits in order to keep the company clean from all sorts of viruses and create a detailed outline of the rules and regulations that all employees must follow to guarantee the safety of the business. After compiling the results of the audits, firms can continue to develop and implement security strategies in order to reduce the risks that have been identified.
If you’re the manager of a firm, these processes may surely sound expensive. However, fret not! Although these processes cost top dollar, they can potentially save firm thousands, if not millions, of dollars from hacking and various other forms of cyberattacks. In a recent survey of cybersecurity planning and expenditure, 66% of 376 respondents who answered a question on cybersecurity spending for 2021 said that their organizations planned to spend more than they did in 2020. It’s no surprise that increased expenditure and investments in cybersecurity continue for firms in 2021 – 2020 shattered the roof with records of cyber-attacks! Due to work from home culture, recent reports claim that malware increased by 358% overall and ransomware increased by 435% as compared with 2019 leading to data breaches costing firms an average of $3.92 million last year!
With the ever-changing and upgrading world of innovations in cybersecurity, it’s hardly exigent to find software that suits a firm’s budget, size and operating scale. In a world wherein hackers can easily hack the bank accounts of companies that have an influence over the share market-planning and implementing cybersecurity measures in the planning stage itself is extremely salient for all firms, big or small. The pandemic has only made it easier for hackers to hack into networks due to lessened security in people’s home computer networks and the continuous modernization in hacking technologies. The future of cyberattacks may seem rather perilous but, with the advent of more sophisticated cybersecurity planning and increased risk and crisis management awareness, firms should be prepared to face any cyberattacks without breaking the bank.
Bibliography/references:
1:https://ciso.economictimes.indiatimes.com/news/37-increase-in-cyberattacks-in-india-in-q1-2020-report/75962696
2:https://www.accenture.com/_acnmedia/PDF-96/Accenture-2019-Cost-of-Cybercrime-Study-Final.pdf
3. Image Credit – https://searchsecurity.techtarget.com/The-ultimate-guide-to-cybersecurity-planning-for-businesses
4:https://www.forbes.com/sites/chuckbrooks/2021/03/02/alarming-cybersecurity-stats——-what-you-need-to-know-for-2021/
Submitted by: Syna Mody, Member of Student Risk Club (SRC)