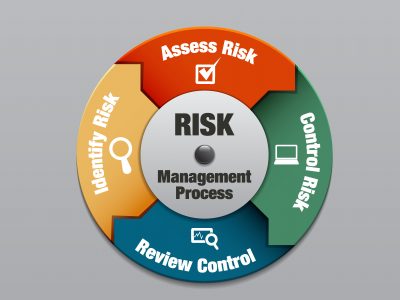
What is Third-Party Risk Management?
TPRM stands for third-party risk management, which involves identifying, mitigating, regulating, and managing risks for a specific organization throughout the lifecycle of the business relationship. The word the third party is also sometimes interchanged with “vendor risk management” or “supplier risk management.”
TPRM is utilized by practically every company, regardless of industry, albeit the laws and regulations differ from one industry to the next.
Third-Party Risk Management process is used to inherently investigate the scope and severity of third party risk. It has quickly evolved from a ‘check-the-box’ routine to a major function, complete with rules, procedures, and technology, in firms that are serious about managing third-party risk. These companies are now taking more comprehensive steps to ensure that their third parties not only follow the rules, but also protect sensitive IT data, avoid unethical practices, maintain a safe and healthy working environment, strengthen supply chain security, effectively handle disruptions, and maintain high quality and performance levels.
Why Is It Important To Manage The TPRM?
To defend your firm, it’s critical to manage third-party risk. For this purpose, tools are used which allow you to track issues like profitability, reputation, regulation, and even litigation.
It is important as it helps to reduce the following risks:
- Cybersecurity risk refers to the possibility of being exposed to or losing money as a result of a cyberattack, data breach, or another security incident.
- Operational risk: The possibility of third-party disrupting business operations.
- Legal, regulatory, and compliance risk: The possibility that a third party will have an impact on your company’s adherence to local laws, regulations, or agreements. Risk to one’s reputation as a result of negative public opinion engendered by a negative public opinion engendered.
- Financial risk: The possibility that a third party will hurt your company’s financial success.
- Strategic risk: The possibility that your company will fall short of its goals due to a third-party vendor.
The Role Included Having A Successful Third-Party Risk Management
1]All third-party collaborations and contracts can be viewed in one place.
2]Before signing a contract, a rigorous risk assessment and due diligence process is carried out.
3]Standardized and risk-reducing contractual terms and conditions
4] Risk-based oversight and monitoring
5] Finally, there will be a formal offboarding process at the end of the relationship.
Sometimes the fourth parties are recognised and evaluated as part of TPRM, such as downstream vendors, suppliers, and contractors used by your third parties. Because risk can flow down the supply chain to the final supplier.
Identifying, Monitoring And Mitigating: The Third-Party Risk
Organizational boards must adopt third-party monitoring strategies, which must be assessed and understood at least once a year. The company must be aware of the high-risk rated services, the volume and risk profile of the complete third-party portfolio, and any major operational loss events that have occurred throughout this process. As a result, it must be aware of the possibility of third-party delivery failure.
Furthermore, such reporting for the board has a qualitative and quantitative aspect in terms of how third parties manage their risk and how they develop confidence in the third party’s capacity to satisfy policies and expectations.
TPRM programmes assist firms in assessing third-party risk exposure, establishing risk management responsibilities to limit risk, and establishing third-party activity oversight. TPRM aids in the initial identification, monitoring, and mitigation of risk.
In an interview with Ethical Boardroom, Greg Matthews’ [Partner in KPMG’s Financial Services Risk Consulting Practice] uncovered effective strategies executives can take to improve TPRM programs and allow third-party relationships to deliver maximum value.
He says in reply to the question,
Q ‘Boardrooms are taking notice and getting more involved in TPRM. How do they gain a better understanding of their third-party relationships and the associated risks?’
In reply to this, he said that organizational boards must adopt third-party monitoring strategies, which must be assessed and understood at least once a year. The company must be aware of the high-risk rated services, the volume and risk profile of the complete third-party portfolio, and any major operational loss events that have occurred throughout this process. As a result, it must be aware of the possibility of third-party delivery failure.
Furthermore, such reporting for the board has a qualitative and quantitative aspect in terms of how third parties manage their risk and how they develop confidence in the third party’s capacity to satisfy policies and expectations.
Q: What steps can executives take to develop effective strategies that will transform TPRM programmes?
In reply to this, he said that Global firms have worked on improving their third-party risk management programmes in three stages over the last five years. Phase one was a design assessment to set the tone from the top, clarify programme governance, define roles and responsibilities following the three lines of defence principle, ensure risk subject matter experts are engaged both pre-and post-contracting and increase ongoing monitoring of third parties through a risk-based programme. The second phase was the implementation of the first phase’s programme, which resulted in two outputs: greater assessment and continuous monitoring operations across the organization and lines of defence, and the second was a reduction in the number of incidents. The second factor was an increase in personnel as a result of these risk management initiatives being delivered. The third phase focuses on risk-based simplification of the programme and employing sophisticated technologies to automate the programme and operations.
A company can achieve streamlining goals by reducing the number of third parties it works with through a preferred provider programme, improving risk assessment questionnaires and gathering information from third parties, and leveraging specialized third-party providers and emerging industry utilities to conduct oversight activities like desktop and onsite reviews. At the end of these three phases, the program’s components must come together to produce a long-term TPRM programme that corresponds with the organization’s Enterprise-wide Risk Management program’s risk appetite and tolerance.
The third phase focuses on risk-based simplification of the programme and employing sophisticated technologies to automate the programme and operations.
A company can achieve streamlining goals by reducing the number of third parties it works with through a preferred provider programme, improving risk assessment questionnaires and gathering information from third parties, and leveraging specialised third-party providers and emerging industry utilities to conduct oversight activities like desktop and onsite reviews. At the end of these three phases, the program’s components must come together to produce a long-term TPRM programme that corresponds with the organization’s Enterprise-wide Risk Management program’s risk appetite and tolerance.
There is a persistent procedure to assess the third party via questionnaire, interview, external party engagement for a background check, and so on in this evaluation procedure.
Conclusion
It assists in the identification of gaps or weaknesses among your third-party vendors and suppliers, as well as the classification and qualification of third-party risk posed by each organization based on the data gathered. If a third party violates these regulations, one organization may be exposed to risks that could result in severe financial, reputational, or legal ramifications, as well as large fines.
Reference
- https://advisory.kpmg.us/insights/risk-regulatory-compliance-insights/third-party-risk/identifying-third-party-risk.html
- https://www.upguard.com/blog/third-party-risk-management-important#:~:text=Third%2Dparty%20risk%20management%20is,data%20breaches%2C%20and%20reputational%20damage
- https://www.riskmethods.net/resilient-enterprise/everything-about-third-party-risk-management
- https://www.gartner.com/en/legal-compliance/insights/third-party-risk-management
- https://cybersecurity.att.com/blogs/security-essentials/third-party-risk-management-explained
Submitted By: Kanchan Rathore – Member of Student Risk Club (SRC)