
Earlier, organizations used to consider the Security Management industry described with adjectives such as “Low Skilled”, “Low Status”, etc. and was used to be considered as a support function possessing limited exposure to the scope of business operations within an organization. But in fact, the Security Management Division is the integral function across entire business operations that has a collective responsibility to ensure the Security Management System is designed, developed and implemented in an effective manner creating a safe and secure environment supporting the organizational objectives and being the First Responders in an event that an unwanted incident was to occur.
Security Risk Management is an integral discipline of the Security Management industry where there are diverse concepts of Risk Management practices specifically designed for the Security Management industry. Security Management personnel must be aware of the fundamental concepts associated with Security Risk Management such as the Security Triangle, Three Stage Risk Management Process, Gold-Silver-Bronze (GSB) Command Structure, Security in Depth (Multi-Stage Security Management System), Five Risk Management Strategies, etc. Some of the Security Risk Management concepts that all relevant personnel should be aware of include:
Security Triangle:
The Security Triangle is a fundamental concept associated with Security Risk Management which consists of three core components: Security, Freedom & Threat. These three core components are interdependent.
In the Security Triangle, Security and Freedom are taken as the tail ends of a see-saw. One among Security and Freedom must compromise for one another, as there is a balance between them that can influence other security management functions. The threat is the Third Function of “The Security Triangle” where it is really important to understand the quantity and quality of the threat as security and freedom cannot be scaled until the threat is fully known. It is the objective of Security Personnel to decide the appropriate balance between Security and Freedom. There will be “More Security” accompanied with “Less Freedom” and there will be “Less Security” accompanied with “More Freedom”. It is an unachievable fact to have “More Security & More Freedom” as it would not satisfy the equilibrium of The Security Triangle.
Various impacts would affect the Security Management System if either Security or Freedom is compromised to a very greater extent which will affect the effectiveness of the security management function and can enforce an unacceptable way of approach towards various aspects and can impart a feeling of disappointment and discontent towards the security management programme.
If there is a change of balance between Security and Freedom where there is “Too Much Security”, then there will be an oppressive attitude characterized through the view of the public’s eyes on the security management function.
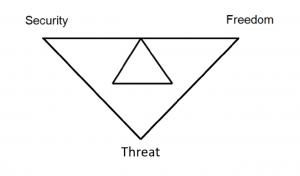
Image 1 – Security Triangle Structure
Three Stage Risk Management Process:
The Three-Stages Risk Management Process is a structured framework in the Risk Mitigation System which allows Security & Risk Management personnel to have a knowledge of risk in a more systematic manner which is implemented in any environment all over the organization irrespective of the hierarchy and range and can be used irrespective of the quantity and quality of the threat.
The Three Risk Management Process consists of Risk Assessment, Risk Control and Contingency Planning where every aspect of Risk Management will be placed among the three. The Process increases the competency in understanding and analysing the risks associated with the scope of operations within the organization and improves in mitigating and responding to the risk with increased efficiency.
- Risk Assessment: The main objective of Risk Assessment is to understand the threat. Risk Assessment is mainly undertaken to Identify and List all Potential Threats and to Give those threats a Comparative Risk Value. In other words, this stage can be described with the question “What are the problems?”.
- Risk Control: The main objective of Risk Control is to create a range of Risk Control Protocols. Risk Control is mainly undertaken to Minimise the Likelihood of an Unwanted Event Happening and Minimise the Impact of any Unwanted Event that does happen. In other words, this stage can be described with the question “What should we do about it?”.
- Contingency Planning: The main objective of Contingency Planning is to regain control of the security operation as quickly and effectively as possible and to return to normal operational status as quickly and effectively as possible. In other words, this stage can be described with the question “What do we do if it goes wrong?”.
The Risk Matrix is a methodology for identifying and categorizing risks where risks are calculated based on two attributes: Likelihood and Impact. The likelihood is the attribute by which risks is calculated based on time. The impact is the attribute by which risk is calculated based on the influence that it would cause when it happens. It is not possible to identify all potential threats but it is essential to categorize the risks based on these attributes by which we can identify the risks on which greater importance should be given of.
The Risk Matrix consists of five sections:
- Low Likelihood/Low Impact: Described as “Not a Problem” and is not essential.
- Low Likelihood/High Impact: Described as risks that do not occur often but has a considerable amount of impact on occurrence.
- High Likelihood/Low Impact: Described as risks that occur in a repeating manner and is considered normal as it does not cause a noticeably significant impact.
- High Likelihood/High Impact: Described as “Crisis Corner” where the risk is certain that it will occur at some point of time causing a major impact and is considered crucial.
- Mid Likelihood/Mid Impact: Described as the section where Risk Management is effectively used by Security & Risk Personnel in generating a positive risk culture.
There are different Risk Matrix that can be utilized depending on the organization’s decision for the indication of likelihood and impact of a potential threat that the organization encounters during its business operations. Some of the examples include:
- Colour Chart Matrix: The colours are utilized to give a clear indication of where potential threats lie within the grid.
- Numerical Value Matrix: A specific number value is utilized to give a clear indication of where potential threats lie within the grid. By multiplying the Likelihood Value by the Impact Value, a specific Risk Value can be calculated for each box.
- Combined Risk Matrix: A combined risk matrix is where both colour chart matrix and numerical value matrix is integrated into a single matrix to measure a potential threat both qualitatively and quantitatively.
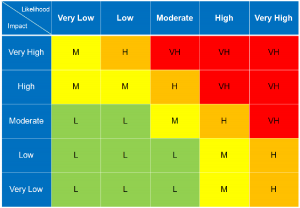
Image 2 – Colour Chart Risk Matrix
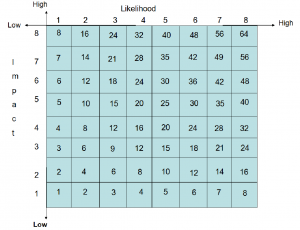
Image 3 – Numerical Value Matrix
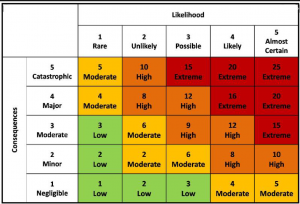
Image 4 – Combined Risk Matrix
Gold – Silver – Bronze (GSB)/Management Pyramid Command Structure
The Management Pyramid/Gold Silver Bronze (GSB) System is a Three-Level Command Structure that serves as a Strategic Function in terms of Incident Response Management. It consists of three divisions mainly “Gold Command”, “Silver Command” and “Bronze Command”.
- Gold Command is described as “Strategic” and is responsible for the strategic planning and designing of the incident response plans and ensuring the plans are designed correctly.
- Silver Command is described as “Tactical” and is responsible to manage the plans in an appropriate manner adhering to the plans.
- Bronze Command is described as “Operational” and is responsible to deliver the plans
The GSB System is implemented in organizations operating in every industry or arena of expertise overlooking various threats of a broad spectrum and it is the fundamental aspect for every incident response operation.
The advantages of the GSB System are that it defines an incident response framework and provides the roles and responsibilities that each level of management should be aware of to implement procedures in controlling and limiting the effects of a crisis or incident event in the organization. Also, it equips the organization to coordinate during the incident response operations avoiding any miscommunication and increasing the organizing effectiveness for all three command levels. The disadvantage of the GSB System is that the failure of any of the three command levels can impact the whole pyramid system causing the incident response to be managed ineffectively.
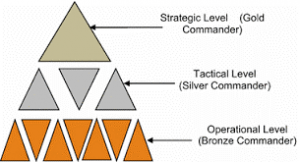
Image 5 – GSB Management Pyramid/Command Level Structure
Conclusion
The above fundamental concepts related to Security Risk Management are essential knowledge for personnel who are required to interface with Security Management responsibilities. Subject Matter Expertise associated with security management is of benefit to every other division within organizations as Security Risk Assessment requires knowledge and awareness of every division, function, and business operations within the organization to design and develop an effective security risk management framework mainly in the way which the organization interests to protect its assets, operations, infrastructure and people from the range of internal and external security threats that it may face. Subject Matter Expertise in Security Management benefits for other divisions especially during emergency response planning to return to normal operation as effectively and quickly as possible and also to reduce further similar occurrences by reducing the likelihood and impact. Hence, effective risk management in security planning will help to make powerful decisions and combat the risk.
References
- HM Government, 2017. National Risk Register of Civil Emergencies.
- Lagadec, P., 2005. Crisis management in the 21st century” unthinkable” events in” inconceivable” contexts.
- Bigley, G.A. and Roberts, K.H., 2001. The incident command system: High-reliability organizing for complex and volatile task environments. Academy of Management Journal, 44(6), pp.1281-1299.
- FEMA National Incident Support Manual – The Federal Emergency Management Agency (FEMA), USA
- ATHE Level 4 Award in Foundations of Security & Risk Management Study Material
Blog Published By: Kartik Unnikrishnan – Student Risk Committee Member, IRM India Affiliate









