Fig. 1 Identifying fraud patterns
Within asset misappropriation, differentiation is typically made between the misappropriation of cash and the misappropriation of inventory and other assets. Some examples of asset misappropriations include skimming revenues, stealing inventory, and payroll fraud. In cash misappropriation, billing schemes are targeted activities within the purchase-to-pay process. There are three different billing schemes: shell companies, non-accomplice vendors, and personal purchases.
Let us have a brief look at these-
- Shell Companies:
Shell company is a fictitious entity without active business activities or significant assets. This is not necessarily illegal, but it is assumed that the shell company was founded solely for committing an economic criminal offense. In order to be able to receive payments, a bank account is usually set up on behalf of the shell company.
There is area of caution to raise a red flag if-
- There is revival of activity in old supplier account (non-active account)
- High purchasing volumes from new supplier
- One-time suppliers suddenly emerge
- There is a single person recording a new supplier in system and handling orders from the supplier.
- Incomplete vendor records in suppliers’ master or instead of address only P.O. box is mentioned.
- Supplier only bills for services.
- There are multiple invoices from one supplier per month, although a monthly payment would be usual
- Supplier operates only by initials or employee’s name is only in initials to avoid identification.
- Supplier master data corresponds to data of an employee (address, bank data, etc.)
- Lack of authorization on PO or authorizations are made after the PO is issued
- Tax amount missing on invoices
- Invoices from one particular supplier always approved by the same employee
- Order amounts are just below the authorization thresholds or the purchases are divided into smaller parts to bypass the thresholds.
- Purchase amount far exceeds that of previous order.
- Invoices are issued for undelivered goods or are higher than order amounts
- Invoices from one particular supplier always approved by the same employee.
- Invoices settled very quickly.
Shell companies are entities that do not engage in conventional economic activities but serve the sole purpose of establishing a scheme to commit fraud.
- Non-accomplice vendor
Although less frequently observed, another fraud is to fool legitimate vendors to unknowingly take part in an illegitimate billing scheme Since the perpetrator does not have access to payments received by suppliers, the so-called non-accomplice vendor schemes take advantage of refunds issued by the vendors. In order to trigger suppliers to send refunds, the fraudster can simply pay vendors twice or redirect payments to the wrong supplier, negotiate refunds for the ‘mistakenly’ paid amounts and pocket those.
The fraudster could also tamper with the ordered quantity of goods and return the excess goods while pocketing the refund, or simply overpay the supplier waiting for the excess amount to be refunded.
Symptoms/Red flags
- Suspicious address of the supplier: same address as another supplier
- High purchasing volumes for a new or unauthorized supplier
- Return of goods
- Supplier invoice is higher than the order amount
- Order amount is higher than invoice
- Overpayment of purchased products or services
- The exact same purchase value is paid to two different suppliers
- Money transactions at unusual times (outside normal business hours)
- Multiple different invoices for the same goods
- Private purchase at organization’s cost
Most perpetrators buy goods or services for their personal use and then erroneously record the invoice as a liability in the company’s internal accounting. In order to conceal the actual purpose of the purchase, purchased goods are declared as business requirements, or fake invoices are submitted. In a shell company, perpetrators are often responsible for authorizing purchase orders.
The perpetrator may either keep the purchases or return them and keep the money. A different form of this schema does not require an authorization of the payment: private purchases with the company-owned credit or purchasing card.
Red Flags to identify–
- Purchase requisition/purchase order amounts are just below authorization thresholds:
- For some purchases, no approval may be required.
- There be small purchases of the same product and an imprecise reason for the received good or service.
- Invoice and payment Invoices, receipt confirmation and order documents do not match.
- Overpayment of purchased products or services
- Purchases are far above the market price
- No or incorrect employee ID on the invoice There is Invoice receipt although the purchase request has been blocked.
- Same person pays the same supplier on the same day the same amount is observed
- The use of different person to pay the same supplier on the same day the same amount can be practised.
- Redirect payment fraud
Legitimate transactions are manipulated in such a way that the payment is transferred to the perpetrators bank account. The employee or an accomplice must have the authorization to change the master data of the vendor. After changing the master data (e.g., bank account), the perpetrator attempts to cover his tracks by changing the bank account
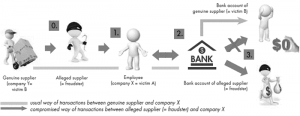
Fig. 2 Redirect Payment Fraud
Some red flags to consider-
- information back to the original information.
- Large budget deviations
- Supplier invoice is higher than order amount
- Adjustments to liabilities (in accounts payable)
- A payment recipient with a name similar to the previous name is entered
- Change of currency between purchase and payment to take advantage of conversion differences
- Doubling and redirecting the invoice
- Same invoice number, same supplier, different amount
There are certain red flags for fraud that can be apparent at the organizational level. Let us analyse some of them-
For senior management, caution can be opted in case-
- Centralized distribution of authority coupled with an autocratic style of management exists.
- Absence of long-term strategic plans
- The routine reporting structure is missing and is done only by exception
- Organisation focuses on profit rather than customer servicing
- No set objectives for meeting contingencies, troubleshooting mode exists.
- Inconsistent disciplining action was taken on violation of company policies
Red flags in transactions
- Does the transaction and its recording in accounts get justified or there is ambiguity?
- Is the person recording the transaction authorized to do so or he seems odd?
- Is there an obvious override of internal controls in recording the transaction?
- Is the transaction in line with organizational operations, goals, and objectives?
- Is the transaction having proper approval from the relevant authority?
- Does the nature of the transaction appear suspicious?
Red flags can be raised if one reads between the data
- The unusual timing of transactions, whether it is outside normal hours, on weekends/holidays, etc.
- Transactions that are occurring too frequently or not frequently enough are suspicious. Each organization has its own operating patterns, and the transactions should be booked accordingly.
- Unusual amounts recorded: Take notice of whether an account has many entries that are large, round numbers. A look at too large value or too less value is important.
- Parties can be questionable; organization has to pay an outside party who may be a related party or vendors who are not easily identifiable in the normal list of vendors.
Red flags to be identified in documents
- Documents are backdated or are altered or found missing
- Whether original documents are missing
- Whether two documents are found contradictory to each other
- Whether signatures are missing on contracts/documents
Red flags in the governance structure-
- The absence of proper controls and encourages frequent overrides
- Lack of intent to remediate gaps in controls
- Management commitment is lacking
- No proper segregation of incompatible duties
- No provision to prevent conflict of interest
- Failure/delay in reconciling accounts
- Loose controls in authorisation of transactions
Thus, we see that there are certain indicators for which one has to look proactively which reinforces the theory of oversight, monitoring, and ability to learn from mistakes. We shall discuss some more sources of fraud going ahead in our next part…
Blog Published By: Ms. Priti Sikdar Executive Vice President at RiskPro India Ventures Private Limited.













