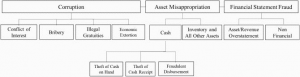
Fraud risk is a lingering reality a threat to combat with. Fraud can manifest itself in many forms. Refer to Fig. 1 represents a fraud tree below-
Fig. 1 Fraud Tree
In this article, we shall limit our discussion to ‘occupational fraud.’ We shall introduce process mining and the red flag approach for fraud detection Occupational fraud can be defined as “crime committed in the course of [the] occupation” or “the use of one’s occupation for personal enrichment through the deliberate misuse or misapplication of the employing organization’s resources or assets”
Corruption, asset misappropriation and fraudulent statements are at the highest level of the fraud tree. Transaction and asset misappropriation are transactional in nature and include the theft or intentional misuse of assets or the abuse of one’s position. Fraudulent statements are defined as the deliberate misrepresentation of a company’s financial statements, timing differences or improper disclosures. Conflict of interests, bribery, illegal gratuities, and economic extortion are included within the category of corruption.
A conflict of interest exists when an executive or an employee has an undisclosed economic or personal interest in a business transaction and influences a transaction to the detriment of organizational interest. Typical examples are purchasing schemes in which a department enters and maintains business relationships with third parties potentially resulting in a conflict of interest.
While bribery involves accepting, giving, or even offering anything of value to influence a transaction, illegal gratuities/gifts change hands ex-post and are considered as a reward and not as an exertion of influence. Economic extortion occurs when employees or managers actively demand something of value in exchange for a favorable decision. The person offering a bribe essentially buys influence in decision-making. There are two common types of bribery schemes: Bid rigging, kickbacks.
Bid rigging: It occurs when vendors influence a competitive bidding process by paying money to those handling the bid. It occurs in the pre-solicitation phase in order to make bids accessible before the submission phase ends. There may be instances when the same person approves a new supplier as well is responsible for payments to suppliers. The possibility is that the same supplier bids under different names. (Fictitious bidders exist)
In a tender process, the winner is generally the last bid for the tender. Through insider connivance, companies are allowed to change bid values. This is feasible if the offer is specific and the number of bidders is small.
- How to look for red flags in bid-rigging?
- When a particular new supplier participates in the auction/bid, prices start falling
- Offers are accepted after the end of the bidding phase
- The wording of the contract clearly favors one supplier
- Lack of transparency in the bid opening
- Supplier is chosen without a clear and competitive advantage
Kickback frauds
Fig. 2 Kickback fraud
In the kickback scheme, the collusion of vendors and employees preferably authorized to approve invoices the vendor issues and submits is established. Invoices are usually either inflated or fictitious, the insider makes sure the invoices are approved for payment and a share of the generated surplus is diverted back to the insider.
1. Sudden business activity with old “sleeping” supplier (sudden activity in non-active accounts)
2. High purchasing volumes from a new supplier
3. Sudden activities in non-active accounts
4. Slow deliveries
5. Supplier provides no typical discounts or special offers
6. Supplier is also customer
7. Only a small number of suppliers
8. A supplier only invoices services
9. Purchase requisition and purchases
10. Higher purchasing volumes seemingly not associated with higher business activity or an increase in stock (rising expenditure on goods and services)
11. Several small orders of the same product (a purchase is divided into several smaller purchases in order to bypass the approval process)
12. Unclear reasons for ordering or few details about the goods received
13. Purchasing value significantly exceeds the last value
14. Sudden activities in non-active accounts
15. No approval for order
16. No goods receipt document.
17. Unusual high stocks and increased purchases from a specific supplier
18. Overpayment of purchased products or services (purchases are above market price)
19. Frequent payments of the same (rounded) amount to a supplier
20. Money transactions outside normal business hours
21. Invoice documented outside normal working hours
22. Double payments
23. Supplier is regularly paid faster than other suppliers (invoices are settled very quickly)
- Payments exceed the average for a vendor
25. Payments exceed the total average
26. The order amount is higher than the invoice
27. Supplier invoice is higher than the order amount.
It is difficult to identify and assess fraudulent activities. One has to know what red flags to look for in the process of fraud identification. How to locate red flags?
A Red Flag is an unusual circumstance or a pattern of anomalies that should alert a reasonable person of possible misconduct. In each such instance, further inquiry and due diligence become necessary to determine if the anomalies are explainable and if not, an investigation is to be conducted. The red flag approach presents hints for unusual behavior, whereas process mining reconstructs and visualizes the as-is business process from the underlying dataset. The combination of these two techniques allows for identification and subsequent visualization of possible fraudulent process instances with the corresponding red flags. Sometimes behavioral traits are good indicators.
Reg flags for money mule schemes (Fig. 3)
- Customer/member account starts to receive transactions that do not appear normal including:
- Overseas transactions
- Purchase of large sums of virtual currency
- A sudden increase in account balances
- Customer opens a new business account with the balance transferred out soon after opening
- Customer opens several accounts at different financial institutions with the high-velocity movement of funds
- Customer receives multiple state unemployment payments
- Customer receives an unemployment deposit from a different state in which he/she previously worked
- Customer receives unemployment payments for numerous employees and the “remit to” name does not match
- Deposited funds quickly wired out to foreign locations with poor anti-money laundering controls
- Customer makes unusual overseas transactions indicating it is for a person overseas needing
financial assistance due to the COVID-19 pandemic
- The customer has documentation from an employer or recruiter using a free email service rather than a company-specific email
- The customer has been asked by an employer to deposit funds into their personal account and then transfer funds via wire, ACH, mail, or money services businesses
- The customer has been asked by an individual for financial assistance to send funds to their personal account.
Behavioral traits are warning signs associated with illegal activity. Some of the common traits are mentioned below-
- Living beyond one’s means
- Financial difficulties
- Unusually close association with a vendor or customer
- Excessive control issues or unwillingness to share duties
- A general “wheeler-dealer” attitude involving shrewd or unscrupulous behavior
Organizations have whistleblowing provisions:
The whistleblowing system requires the company to raise awareness among their stakeholders to recognize the characteristics and red flags of fraud, as well as how important it is for the stakeholders to take part to mitigate the wrongdoings by reporting their findings.
Fraud crime is increasing by the day. Research analysts have proven that crimes created by insiders are more in magnitude and have a devastating impact on the organization. In this series of three articles, we will traverse the different modes of propagation of occupational frauds. Along with that, we shall know how to identify red flags and organise mitigation in the form of fraud assessments.
Blog Published By: Ms. Priti Sikdar Executive Vice President at RiskPro India Ventures Private Limited.